What to Do If You Believe You Have Fallen for a Phishing Attempt
If you suspect you have fallen for a phishing attempt by providing any University information or account credentials, or have downloaded suspicious content, please contact your local academic technology team or the IT Service Desk at 973-655-7971, option 1, or by email at itservicedesk@montclair.edu to report the incident and be provided with additional guidance.
If you provided any financial or personally-identifiable information such as bank account or social security number that could potentially be used for identity theft, please contact University Police at (973) 655-5222 or msupolice@montclair.edu to file a report.
Please Note
If you used or provided your NetID username and password in response to a phishing scam, immediately change your NetID password via the NetID Account Management Center.
Phishing is an email, phone call, or text message based attack that is sent with the intention of deceiving the recipient into providing information.
Potential phishing emails are an information security concern, however, only if the recipient has reacted to the attempt by:
-
-
- Providing any information or credentials via email reply or clicking on a link in the email and submitting information to a web page or form.
- Downloading and/or opening any attachments in the email or downloading any files resulting from clicking on a link in the email.
-
SPAM is unsolicited email as related to advertising, service offerings, social or political causes, etc. SPAM will not typically ask you to provide any information or ask for your personal or account related information via a reply or upon clicking a link. SPAM can simply be deleted or you can mark the message as SPAM in Gmail or in your preferred messaging client. While it may be annoying to receive, SPAM is not generally considered an information security concern and does not need to be reported to the IT Service Desk.
If you only opened (read) but did not otherwise interact with a potential phishing message as described above, the message does not need to be reported to the IT Service Desk. If you are using Gmail, you can report the message to Google:
-
-
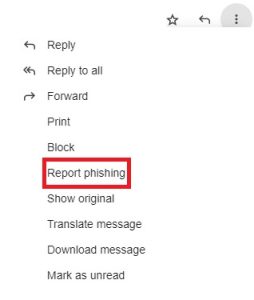
- While viewing the message, click on the three vertical dots on the upper-right of the message.
- Click “Report phishing”
-
If this does not automatically remove the email from your inbox, you may proceed to delete the email.
If you did interact with the message (i.e. click links, open attachments, or provide information), please see the first section above, “What to Do If You Believe You Have Fallen for a Phishing Attempt“.
- Suspicious sender’s address that may imitate a legitimate business
- Generic greetings and signature and a lack of contact information in the signature block
- Spoofed hyperlinks and websites that do not match the text when hovering over them
- Misspelling, poor grammar or sentence structure, and inconsistent formatting
- Suspicious attachments or requests to download and open an attachment
- Spearphishing: Phishing targeted at an individual by including key information about them
- Whaling: Phishing targeted at a high-profile individual to steal sensitive and high-value information
- Vishing: Phishing via voice communication to entice the victim to engage in conversation and build trust
- Smishing: Phishing via text messages to get the victim to click on a link, download files and applications, or begin a conversation
- Be on the lookout for common signs of phishing
- Check both the display name AND the email address. Attackers often attempt to distract victims from the false email address (bob.jones@msu.com) by including a real display name (Bob Jones).
- Attackers use publicly accessible directory information to appear as someone of authority such as your manage or the university president.
- Prevalent spelling and grammatical errors. Legitimate business and marketing brands take communication seriously and legitimate emails usually do not have a prevalence of spelling mistakes or poor grammar.
- False information such as department names. If you never heard of the “Office of Student Registration”, it is likely because it doesn’t exist. Check with the campus directory.
- Requests to provide personal information or credentials via an email response or form. All central and distributed campus Information Technology resources are trained not to ask for a user’s personal credential information (i.e. password to your NetID account) nor should you provide it. Ever.
- Check both the display name AND the email address. Attackers often attempt to distract victims from the false email address (bob.jones@msu.com) by including a real display name (Bob Jones).
- Do not trust links in email (or texts)
- Attackers often include embedded links in an attempt to redirect you to a malicious site. The site could be a form asking for you to enter information, create an account, login using your credentials, etc. There are many different examples, however, they are all designed to steal important information from you.
- Never trust embedded links (highlight text that appears as words and not a URL/site address) in an email or text message. Always check the full URL to see if it appears suspicious. Do not open/follow the link if you are not sure.
- To check the URL of an embedded link (The Hover Over Method):
- From a computer, move your mouse pointer over a link without clicking. The actual web address of the link should appear at the bottom of the browser window or in a pop-up.
- From a mobile device running iOS (Apple) or an Android OS, you can evaluate embedded links by pressing and holding the link down with your finger or stylus. A pop up dialog should appear and then let go. The dialog should show the full URL of the embedded link and other options.
- To check the URL of an embedded link (The Hover Over Method):
- A safer approach is to manually type a known website into your browser. For example, if you receive an email purporting to be from your bank, use your browser to type in the address of your bank directly instead of clicking the link.
- Do not trust attachments
- If the attachment is unexpected or has a suspicious name or file extension, the sender’s account may have been compromised. Call the sender to verify the attachment before opening.
- Do not call phone numbers listed in emails from unfamiliar senders
- Reference a reliable source such as a billing statement or go directly to the company’s web site to obtain the number.
- Assess the greeting
- Was the greeting vague such as “Valued Customer”? Legitimate businesses that have your customer information will often use a more personal greeting with your first and last name.
- Be mindful of the tone
- Attackers typically attempt to create a sense of urgency to trick the recipient into thinking that they must take action immediately which also serves to distract you from assessing the legitimacy of the request.
